It’s not uncommon to find the traditional vulnerability assessment report buried under the CISO family picture, compliance books, and his latest blood pressure test. These reports highlight the never-ending battle between security and IT about what’s more important: risks to servers and endpoints, or keeping the environment up-to-date and secured. There are even problems within the ranks of each unit. Dysfunctional processes, lack of efficient communication, and rudimentary tools put even more pressure on the CIO and CISO.

Recently we visited a client with around 50K assets. He had 600K vulnerabilities to tackle. The poor guy said that IT won’t let him patch 90% of them. The remaining 10%? Sent off to patching purgatory, which means they’re not seeing mitigation in 4-5 months. The worst part is that the security team won’t know a vulnerability is still valid or resolved until after the next vulnerability assessment scan report, which will include the new vulnerabilities, plus the ones that were not previously mitigated. Patching pressure compounds and the stress piles up.
We saw how product and process failures led to the establishment of a new market, which stands in the middle of IT and security, that tries to reduce the number of critical CVEs to handle. At Vicarius, we mitigate these issues with a modern, personalized, consolidated, and predictive solution. A new era of Machine Learning and Automation brings AI to the vulnerability management battlefield.
We had a few guiding stars along the development process:
Proactivity over Reactivity
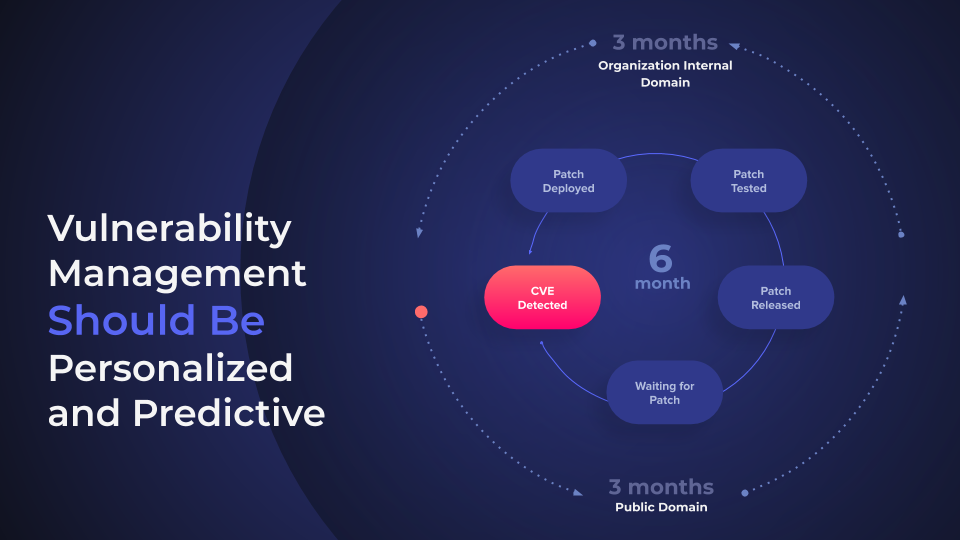
The process of vulnerability management—disclosing vulnerabilities, waiting for a patch, testing the patch, installing it, repeat—is reactive. We wait for the next software to be hacked in order to protect it. No more waiting to understand threats, or tackle them only when the vendor is ready.
Consolidation over Orchestration
Advanced organizations have 2-4 different products to perform scanning, prioritization, contextualization, and remediation. To make things more complex, there are orchestration products to integrate them. This multi-product, multi-department, and multi-disciplined practice has to be united!
Automation over Manual Labor
As the number of systems, vulnerabilities, and patches grow, companies have significantly grown their risk management, IT, and security teams. A ServiceNow report stated that 69% are planning to extend their patching team. We don’t believe people alone can solve this technology problem. Proactivity and consolidation are the base automation, and this is where Vicarius is heading!
Contextualization over Data Correlation
As the network is an ever-changing environment, it is difficult for organizations to understand connectivity, privileges, and other attributes that define the probability a threat will be successful. This is in large part why unmitigated vulnerability is involved in over half of the breaches we read about. Contextualization of vulnerabilities to determine what should be fixed first and last is desperately needed. This contextualization should be automated and thorough.
In the next few weeks, we will drill down into each part of the Vicarius system to show you how we built our solution to tackle this problem.
In the meantime, you can learn more about this with my discussion on Paul's Security Weekly:
Happy patching!



