The public’s favorite government agency, CISA (not the CIA) has recently added five new vulnerabilities to its Known Exploited Vulnerabilities Catalog, the living, breathing, exponentially growing list of vulnerabilities that have seen active exploitation in the wild.
Perhaps most interesting (perplexing?) is that 3 out of the 5 vulnerabilities are from 2014….2014!...like, 8 years ago 2014….launch of the Apple Watch 2014…
I want to do a little dissection on each of the five vulnerabilities added to the catalog. (Don’t worry, everything is sanitary here). I’ll break them down by vendor, starting with Microsoft.
Microsoft
This is a use-after-free vulnerability in Internet Explorer 9 and 10 affecting the MSHTML CMarkup component. The flaw allows remote attackers to execute arbitrary code by abusing a dynamic memory mechanism. If a data set is moved to a different location but the pointer is not cleared—and remains referencing the freed memory—the result is known as a dangling pointer. The attacker can abuse this to execute remote code.
This is an elevation of privilege vulnerability in Windows kernel-mode driver (win32k.sys). With a successful exploit, an attacker can hijack the system and install programs; view, change, or delete data; or create new accounts with full user rights. Workstations and terminal servers are most at risk.
Apple
A type confusion vulnerability, this flaw allows processing of maliciously crafted web content, leading to arbitrary code execution in a multitude of Apple products.
Another type confusion vulnerability, the flaw also allows processing of maliciously crafted web content, leading to arbitrary code execution in a multitude of Apple products.
OpenSSL
Also operating under the pen name ‘Heartbleed’, this vulnerability is due to a malfunction in the TLS heartbeat extension. It allows an attacker to retrieve private memory of an application that uses the vulnerable OpenSSL library.
TOPIA Integration
To be included in the catalog, the vulnerabilities must meet the following criteria:
- The vulnerability has an assigned Common Vulnerabilities and Exposures (CVE) ID.
- There is reliable evidence that the vulnerability has been actively exploited in the wild.
- There is a clear remediation action for the vulnerability, such as a vendor provided update.
For each of these criteria, there is a corresponding xTag in Topia to help identify the vulnerability.
- #known_vulnerability
- #has_exploit
- #has_patch
(It’s almost like we anticipated it… 😜)
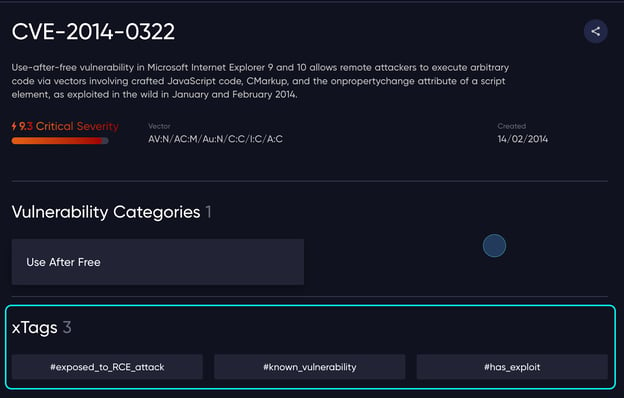
An example from the Vicarius Research Center showing xTags for a specific CVE
Mitigation
The release states: “Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice.”
Unsurprisingly, the recommended remediation guideline is to apply the vendor updates. Many complications stand in the way of organizations implementing and deploying the latest patches. But it goes to show how straightforward hygiene practices can deter threats, reduce your overall risk, and improve your security posture.
So, what can you do from here? Well, you could throw on some Iron Maiden, crack open a couple Red Bulls, and swing open the Research Center doors for more information on each of the five vulnerabilities. There’s a whole host of resources from affected operating systems to advisory and patch links.
Time is ticking and hackers are itching, so get patching!

Resources:
https://www.cisa.gov/known-exploited-vulnerabilities-catalog



