The scene is Troy, an ancient city situated in what is now Turkey, and long the bane of the Greek army. After a fruitless 10 years of battle, the Greeks developed an ingenious plan to deviously win the war.

A huge wooden horse, (the emblem of Troy) was constructed and given as a concession to the Trojans. The Greeks sailed away, and the people of Troy wheeled their trophy inside the city walls and celebrated the victory. Or so they thought.
Inside the horse, an elite squadron of Greek soldiers is quietly waiting for night to fall. As soon as the city fell asleep, they surreptitiously opened the city gates for the Greek army that returned undercover to win the war.
10 centuries later, it isn't huge wooden horses that penetrate our defenses, but criminals behind screens that maliciously exploit legitimate software you'd never think to mistrust. By misusing tools that exist only to better and advance the digital experience, they gain access to all the information you hold dear.
In this article, we're going to dive into the deep ocean of hacking techniques, and try to simulate what it looks like when someone abuses the executable.
A quick recap: executables are special files that actually cause the computer to do things - to execute tasks.
`mimikatz`
is an extremely powerful tool developed by Frenchman Benjamin Delpi. In just about 2 minutes, Mimikatz can be installed, and then by exploiting a Windows executable called lsass.exe, it'll steal all your passwords.
To really understand how Mimikatz works it's magic, I'll run it alongside a tool called x64dbg that'll provide real-time data on what Mimikatz is doing on my computer.
Once installed, it takes only two lines for Mimikatz to steal your passwords.
Number 1 :
`privilege::debug`
Mimikatz needs administrator privileges in order to access other running processes (currently working programs in layman's terms). `privilege::debug` gives Mimikatz the authority it needs.
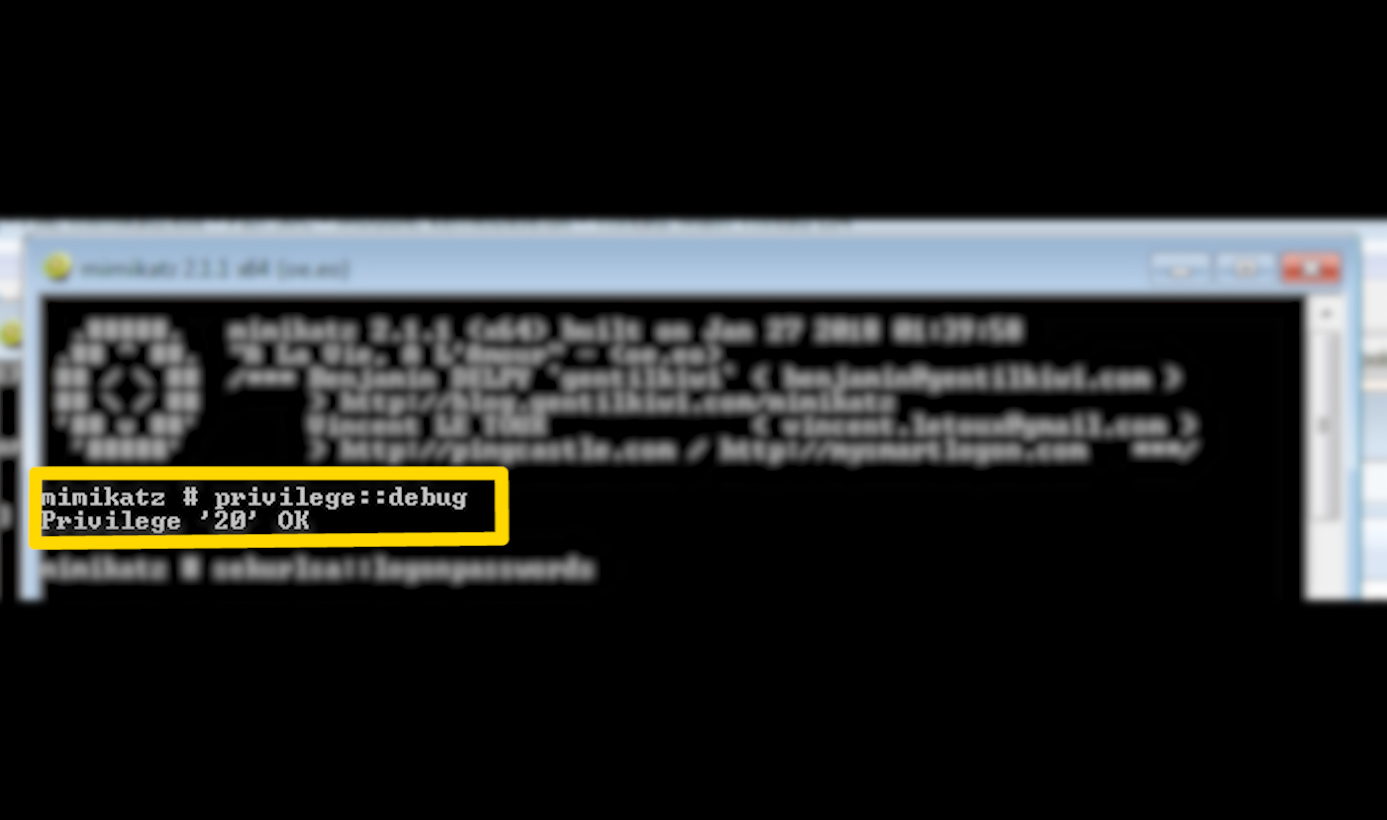
Number 2 :
`sekurlsa::logonpasswords`
This is the integral part of Mimikatz.
To understand how this command works, we need to break it into two parts - `sekurlsa` and `logonpasswords`.
`sekurlsa` is the part that exploits the `lsass.exe` process. `lsass.exe` (stands for Local Security Authentication Server) is an important Windows authentication executable that stores your login details so you don't have to enter your password repetitively while using the computer. It's extremely useful and aims only to improve the user experience. Mimikatz ruthlessly abuses it and steals the chunk of password data it holds.
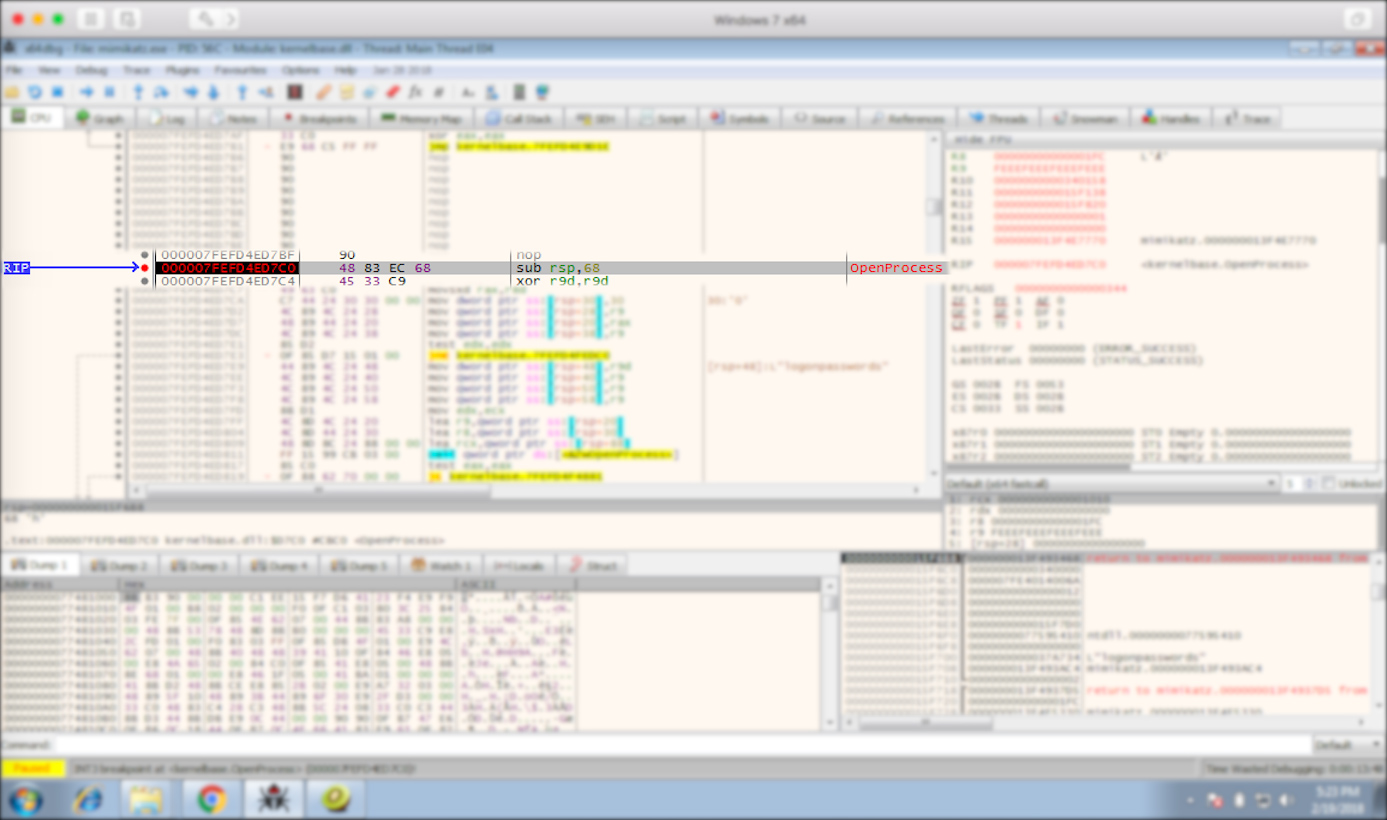
You're looking at a screenshot of x64dbg, a useful tool that lists (among other things) all the functions a program calls (uses). Highlighted is a line that details a Mimikatz call to a Kernel32 (library) function called OpenProcess, which Mimikatz uses to essentially open lsass.exe so it can wreak havoc and steal your data.
`logonpasswords` is just as ingenious as it's precursor. It translates the chunk of data passed to it by `sekurlsa` into plaintext passwords you and I can read.

It's that simple. All you need is an internet connection, some free software, and behold - the keys to the information empire are yours.
The follow-up question is glaringly obvious. How did Microsoft respond to the gaping hole in Window's security? Initially in 2011 - they didn't. Eventually, they released a patch in 2013, but Mimikatz is smarter and is beloved by hackers till today.
This is precisely why you need Vicarius's Topia - because without it; all those cute family pictures and credit card details and PINs and passwords - they're all compromised.



