The most ubiquitous term in the cyber world right now is probably software. What is a software, how does it work, and why this knowledge is of crucial importance to the systems that keep our PCs safe.
The Merriam-Webster dictionary defines software as "programs for a computer." A program is a set of specific instructions, therefore software is essentially a set of instructions for a computer, but this is a simplistic understanding. To comprehend what's actually going on behind the scenes, there's some nerdy stuff we need to cover.
First - executables. These are special files that actually cause the computer to do things - to execute tasks.
Secondly - modules. This is the definition of a unit, or distinct part of a program. A typical program will consist of a bunch of different modules that work together.
Thirdly - operating system libraries. A library is a collection of resources a program or module might use. Imagine you're baking a cake, and the recipe calls for you to mix the eggs and flour, but you don't want to do it by hand - so you head for the kitchen cabinet (library) and utilize the electronic mixer (resource). An operating system, or OS library is just a bunch of functions related to the OS, for example, getting the current date and time.
Finally - system calls. These go hand in hand with OS libraries - a system call is simply the way a program asks the OS, or a different library for a particular resource.
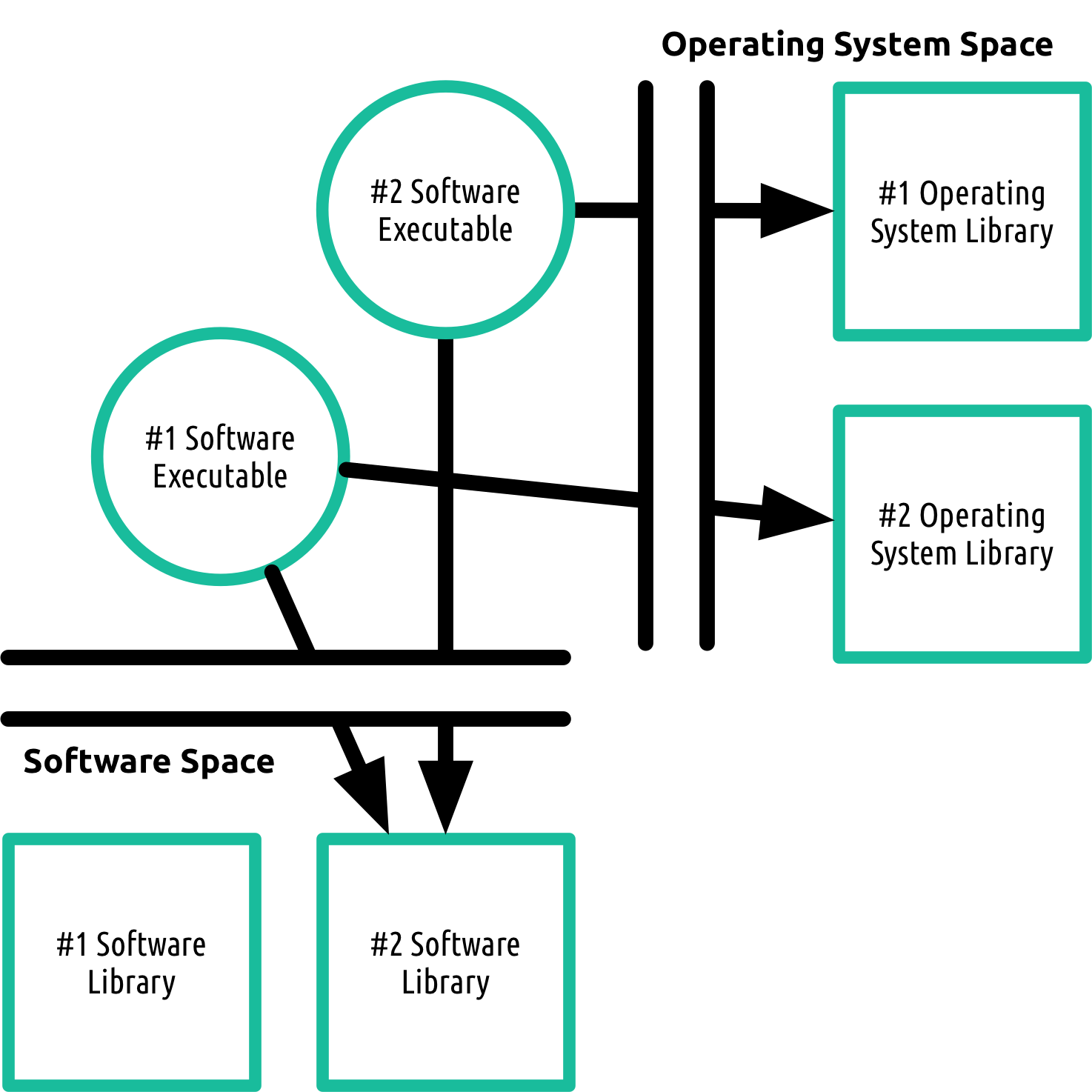
Take WhatsApp, for example. It is a piece of software, a program that instructs a computer to send messages. Under the hood - we'd find the executables, which tell the computer exactly what to do. We'd find a bunch of different modules - perhaps one for sending pictures, one for receiving texts. Inside those modules, we'd find system calls to the OS time resource, so we can timestamp our messages.
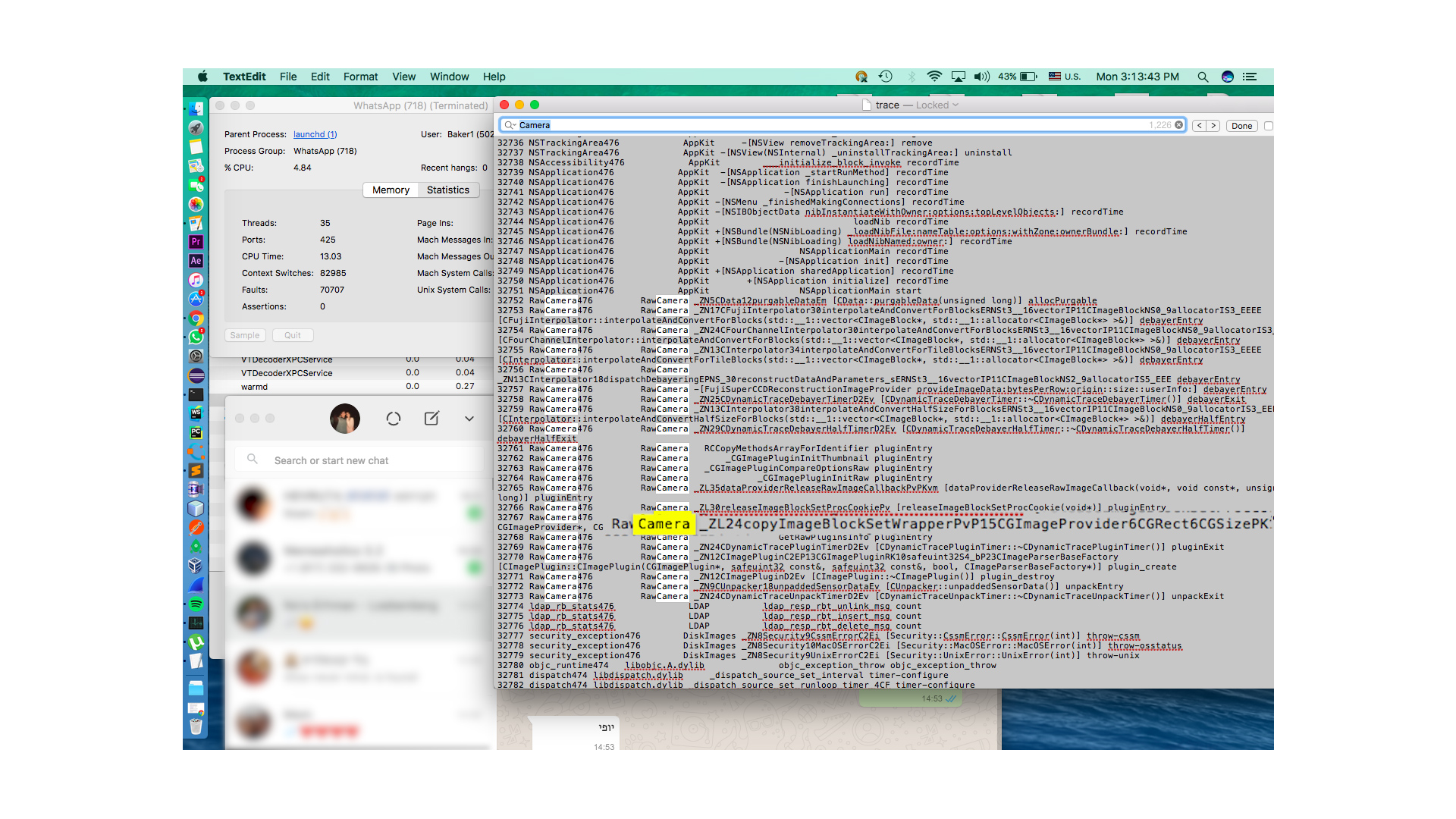
The above image is the result of a command called 'dtrace', that can print (among other things) all the system calls a software uses. Highlighted are requests to a library called RawCamera, because what's WhatsApp without some good selfies.
Software is in essence an intricate puzzle of all these things, that work together to provide us with the apps and services we know and love.
After understanding how software works, we can now analyze the different security risks associated with it.
There are three main malicious way hackers can exploit the software structure to do all sorts of nasty things on your computer.
A cunning coder can edit an executable to contain additional commands, perhaps in a addition to sending your messages to their proper recipients, it'll send them to the hacker too.
One can also impersonate an executable, and instead force the computer to carry out a set of instructions that steal your credit card details.
A persistent programmer can also carry out their own system calls, and gain access to critical system functions - and potentially hold your computer, with all 10 GB of family pictures at a ransom.
Hackers use techniques and systems that have legitimate usages in a perverse way - this is why it's so difficult to prevent attacks : a hackers system call looks alarmingly similar to a kosher one.
The Vicarius Team has in essence reinvented the wheel with their approach to cyber-security. Instead of just simply erecting hypothetical walls of defense, they hunt down potential vulnerabilities, and assign them a risk level using a complex system.
Now, when a hacker hunkers down and tries to break in, a huge, slobbering rottweiler is waiting at the door, anticipating the attack.
As Jack Dempesy, former world heavyweight champion says, "the best defense is a good offense".



