Vulnerability prioritization is a key aspect of vulnerability remediation and threat tracking. It allows companies to strategize their mitigation paths for security weaknesses based on the criticality of cyber risk with the right organizational context.
Why do we need to prioritize vulnerabilities?
In order to understand the reasons behind security vulnerability prioritization, we need to go back to where it all started: the line in the sand between the security professionals' and IT teams' responsibilities.
The vulnerability management tools security teams use spit out a lot of data. Let's take for example one vulnerability on one golden-image app running on 200 active assets. Boom - there we have 200 lines in our vulnerability assessment report. In reality, the multipliers are much more aggressive, so even with a small environment of 500 computers, it can easily reach a few hundred thousand vulnerable spots. From a cybersecurity perspective, we want to be nothing less than 100% clean, covering any web app, configuration, or software-based CVE (Common Vulnerabilities and Exposures) threats. However, because we are also dealing with internal business needs and politics, we can't patch or mitigate everything as the impact of these changes may impose business functionality, instability, and interference to employees' work. One way to reduce this tension between business continuity and strong cyber hygiene is through the process of vulnerability prioritization, which identifies the most critical threats from the assessment report.
There are a few generations of prioritization methods:
Gen 1 - CVSS-based Prioritization
Every line item we will get from our vulnerability scanning report has an attribute called CVSS score. This attribute, which stands for Common Vulnerability Scoring System, is the CVE risk score as determined by the US National Vulnerability Database (US NVD) for new vulnerabilities. CVSS base score is a combination of 2 factors: threat and exploitation. The combination of them creates the vulnerability severity. The most naive way to prioritize a scan is to sort the vulnerabilities by their CVSS score. Using a pre-determined rule of thumb to run patching activities or other mitigation actions on the top 10 CVEs—anything which is above 8 (CVSS is 1-10 scale), or all critical vulnerabilities according to NVD—we can reduce the scope of our risk reduction measures. The limitations of this method are obvious. Our results are not based on any information that indicates the chances of exploitation based on the peripheral context in the outside world, or even more important - inside the organization.
CVE Report
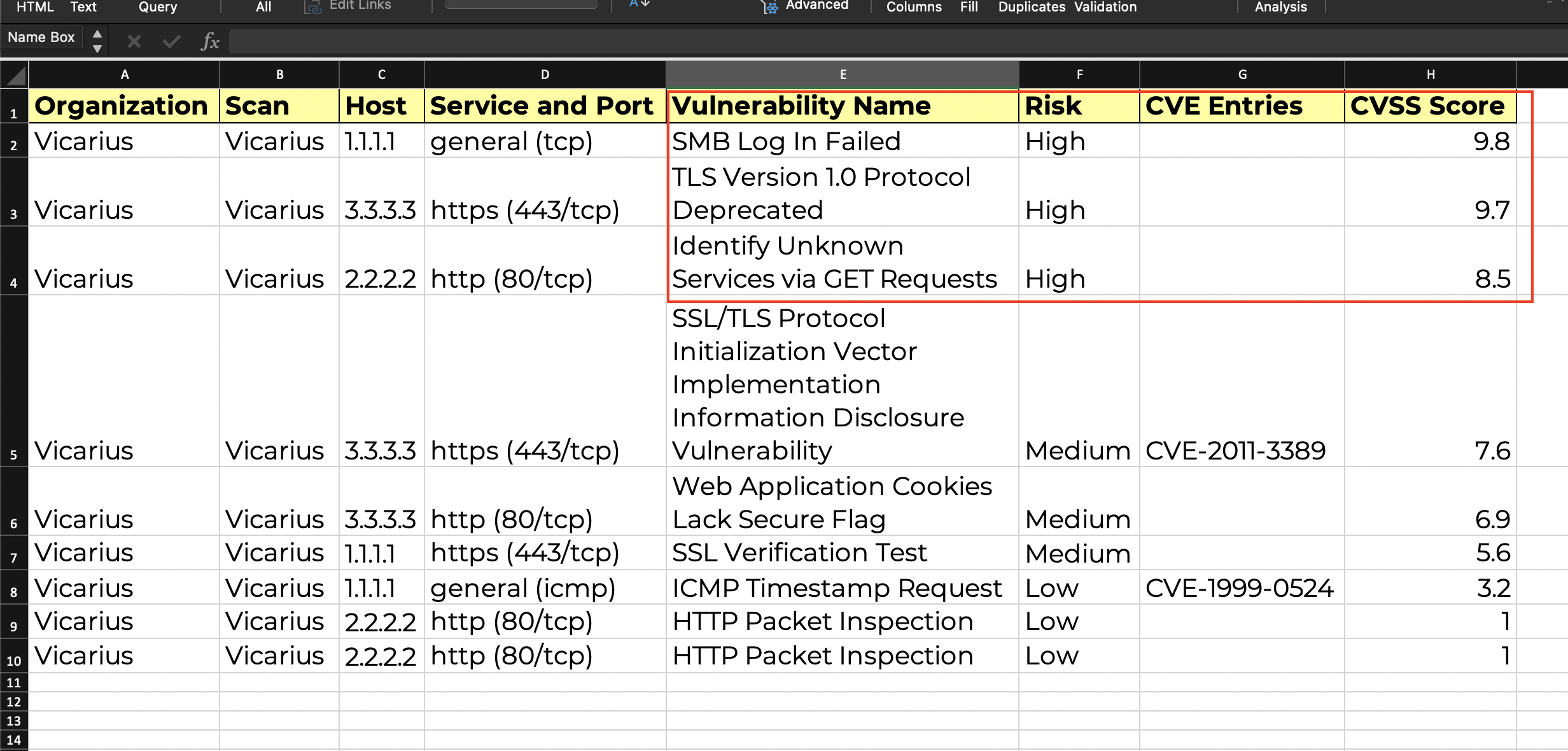 CVE report sorted by CVSS Score
CVE report sorted by CVSS Score
Gen 2 - Subjective Prioritization
As the organization's attack surface became more complex, and our simple on-prem infrastructure of endpoints and servers suddenly got an influx of remote assets and dynamic real-time cloud layers, the number of vulnerabilities exploded. A new way of prioritizing threats was needed, with two new data points:
- Threat intelligence data feeds - external information about what's going on in the world with a given CVE. For example - does a certain threat have a publicly available exploit? Or is it being exploited on the dark web by threat actors?
- Manual or automated asset tagging - this process integrates into the risk management process the asset importance according to the decision of the vulnerability management program manager or machine learning algorithms. So if a certain asset is a sensitive database, or is being used by the CEO, it will have a greater weight in our sorting algorithm. Of course, this subjective approach can create false positives in our risk reduction strategy, as most of the time, the real exploitation factors are not necessarily associated with the business function of the device in the network, but rather on the execution properties of a device or software in our network.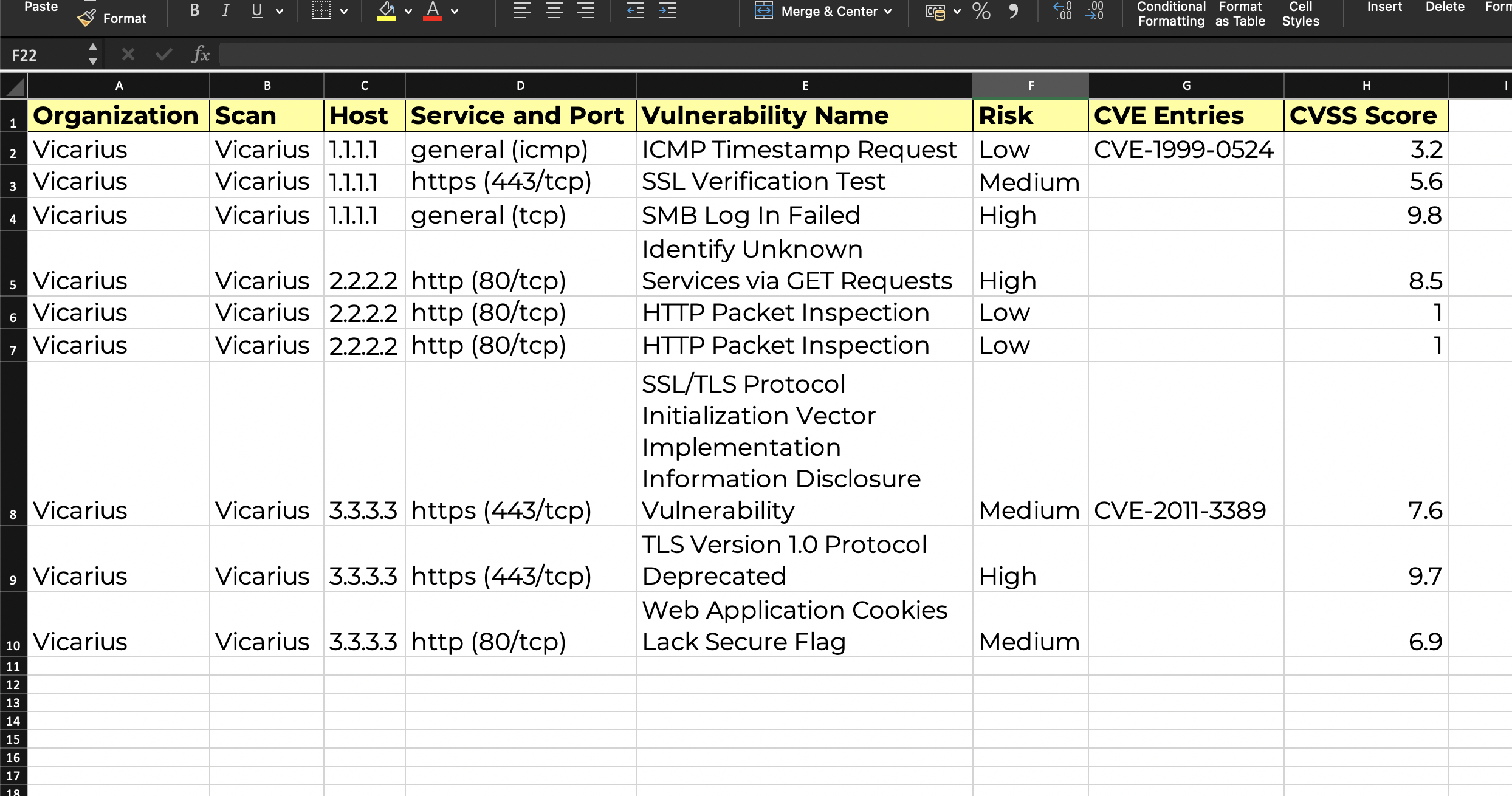
CVE Report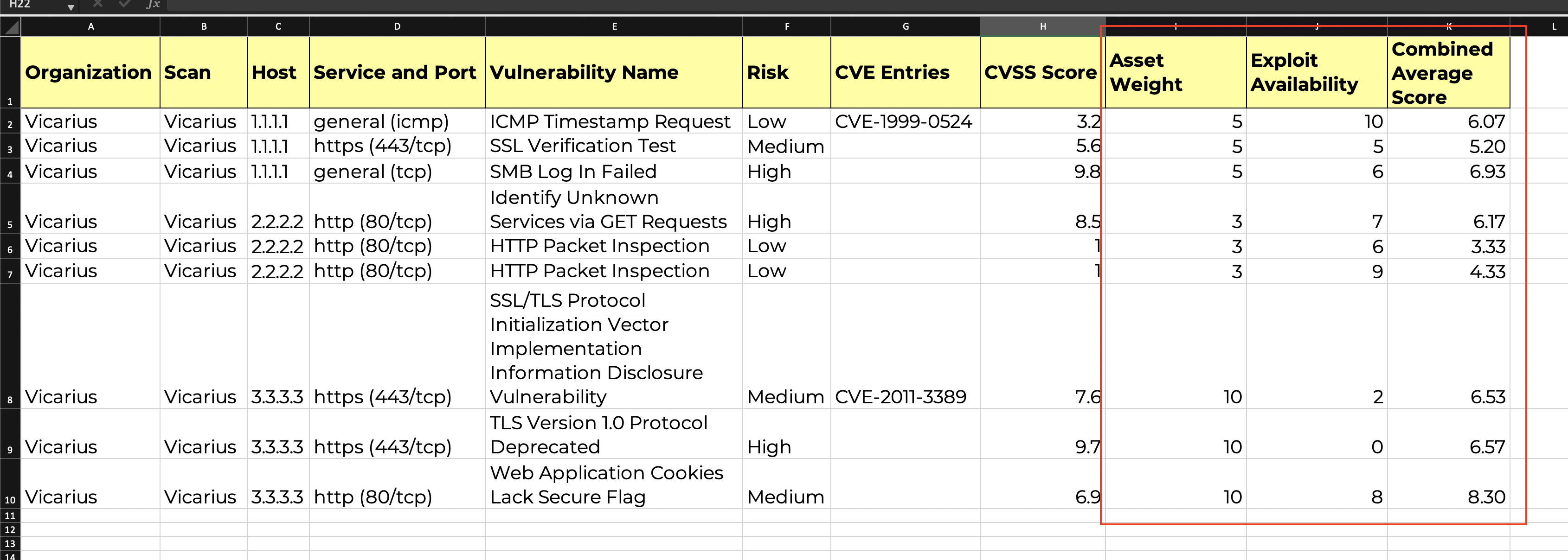
CVE report with critical assets tagging and external data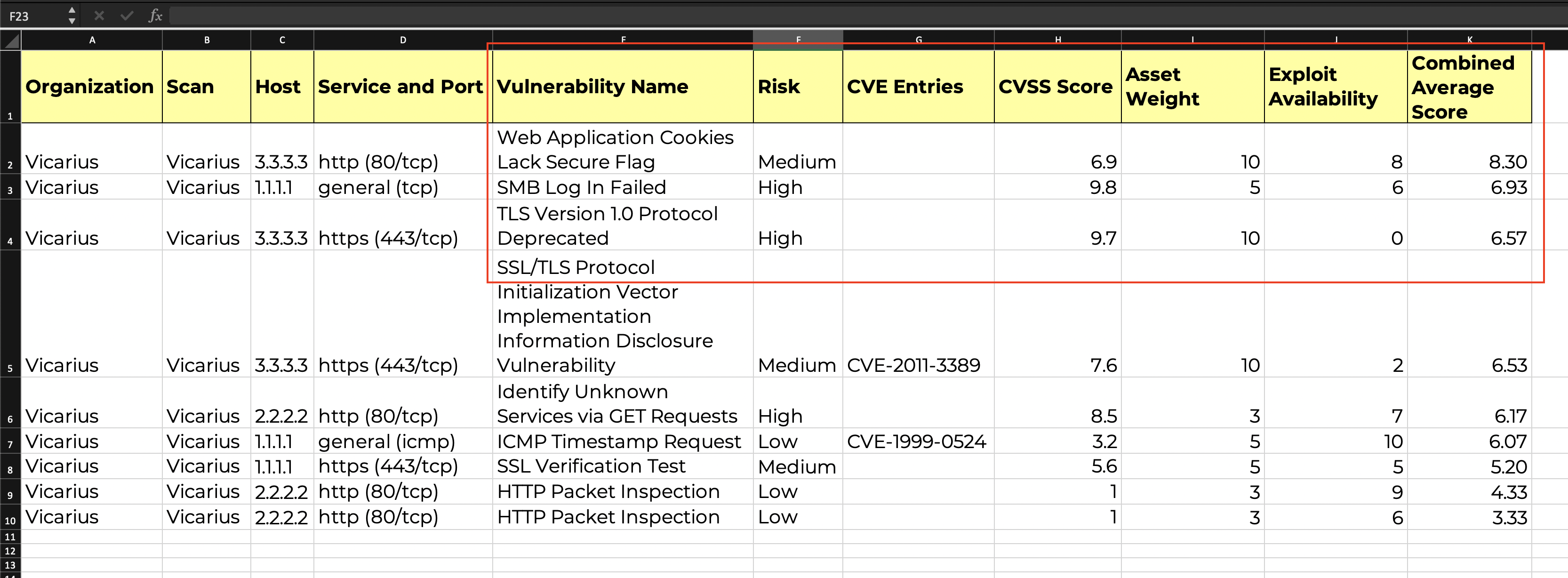
CVE report sorted by custom risk scoring
Gen 3 - Asset Context Prioritization
With the attack surface evolving, new prioritization products emerged trying to integrate asset and app context into the risk management lifecycle. This new product line, defined by Gartner as Asset Context Prioritization, and has two main approaches.
1. Integrated products - tools that gather data from vulnerability scanners, security, and SIEM to draw a wider picture of the vulnerability context.
2. Sensor-based products - products which collect peripheral assets data from the endpoint and ingest it into insights mainly around asset tagging. These products still rely on threats gathered from the vulnerability scan.
The benefits of this approach are clear. We can finally tag assets efficiently and have some contextual data - but can we do better?
Gen 3.1 - End-to-end Automated and Usage-based Prioritization
Yes, we can! Relying on external data sources to collect risk data is not enough. Firewall logs or incident response data from our endpoint security product can't provide us with the relevant information to identify which app imposes a greater risk. But the latest version of prioritization products can: understanding software and asset inventory, collecting customized telemetric data, and generating insights for digital entities, as seen on the endpoints. We finally got it, no need for manual and error-prone labor, no need for third-party integrations. We have it all under the product (oh yes, it's also an end-to-end solution, no need for another vulnerability assessment product!) - Vulnerability Prioritization 3.1 is here.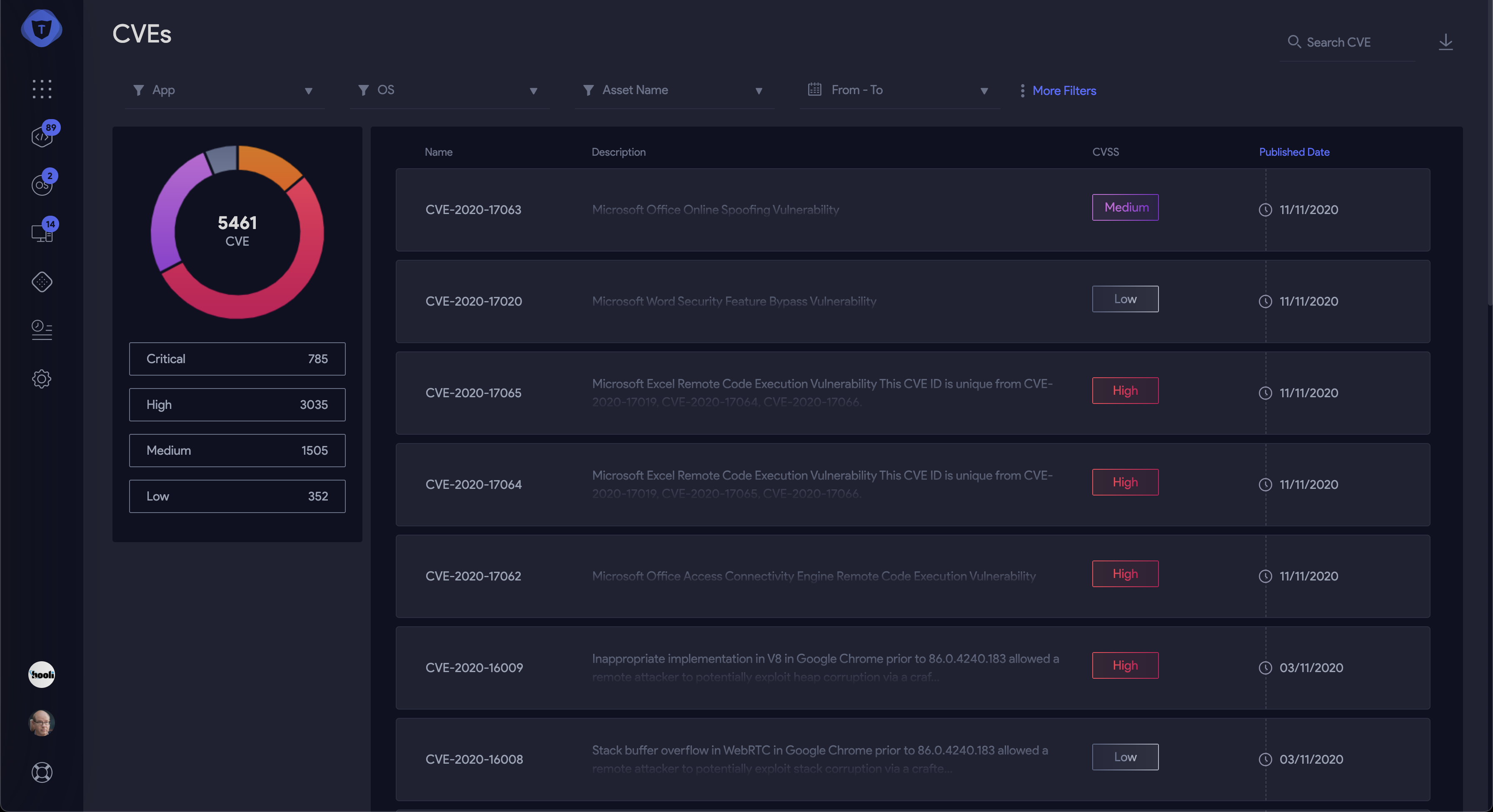
TOPIA - All CVE Threats 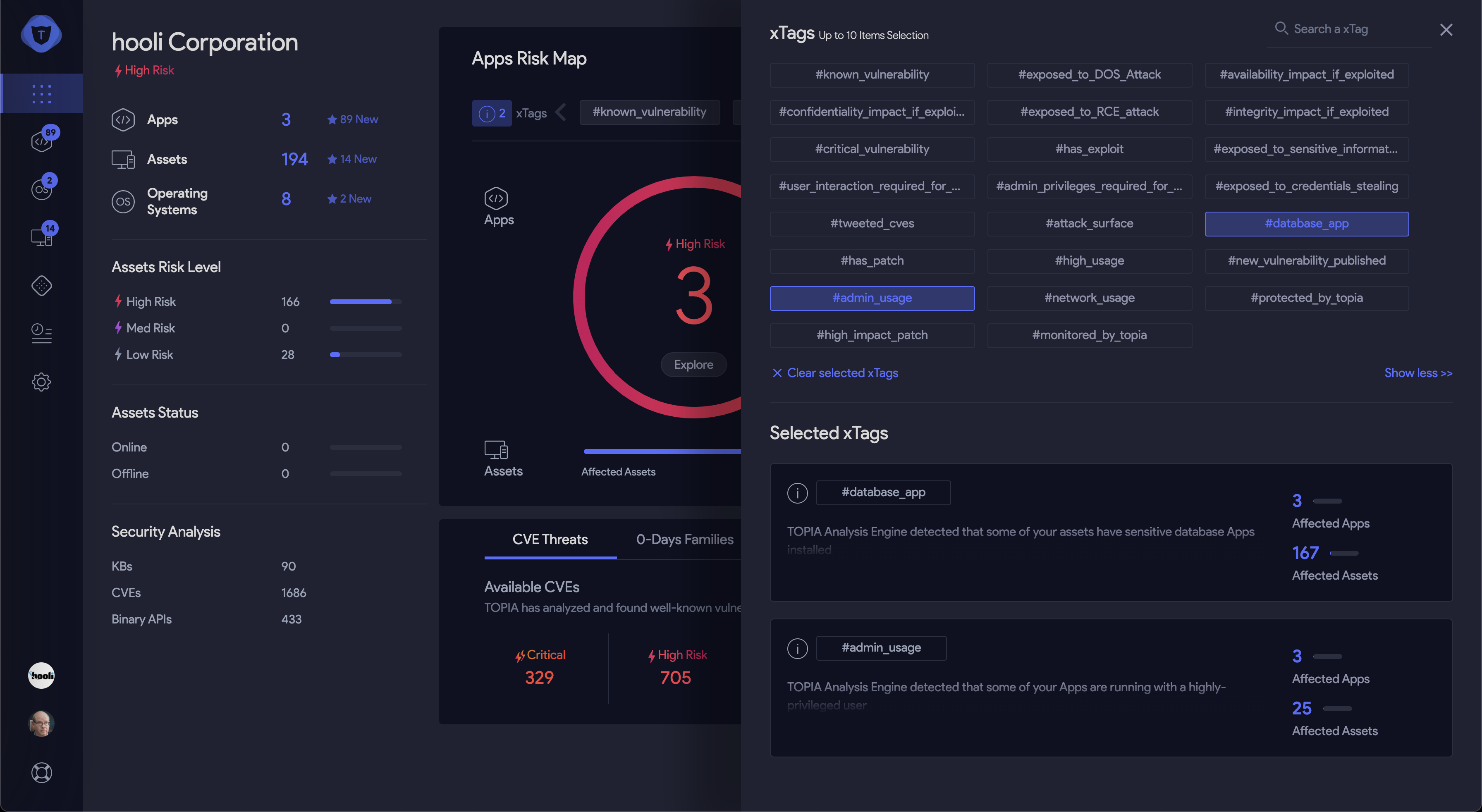
xTags - internal and external risk factors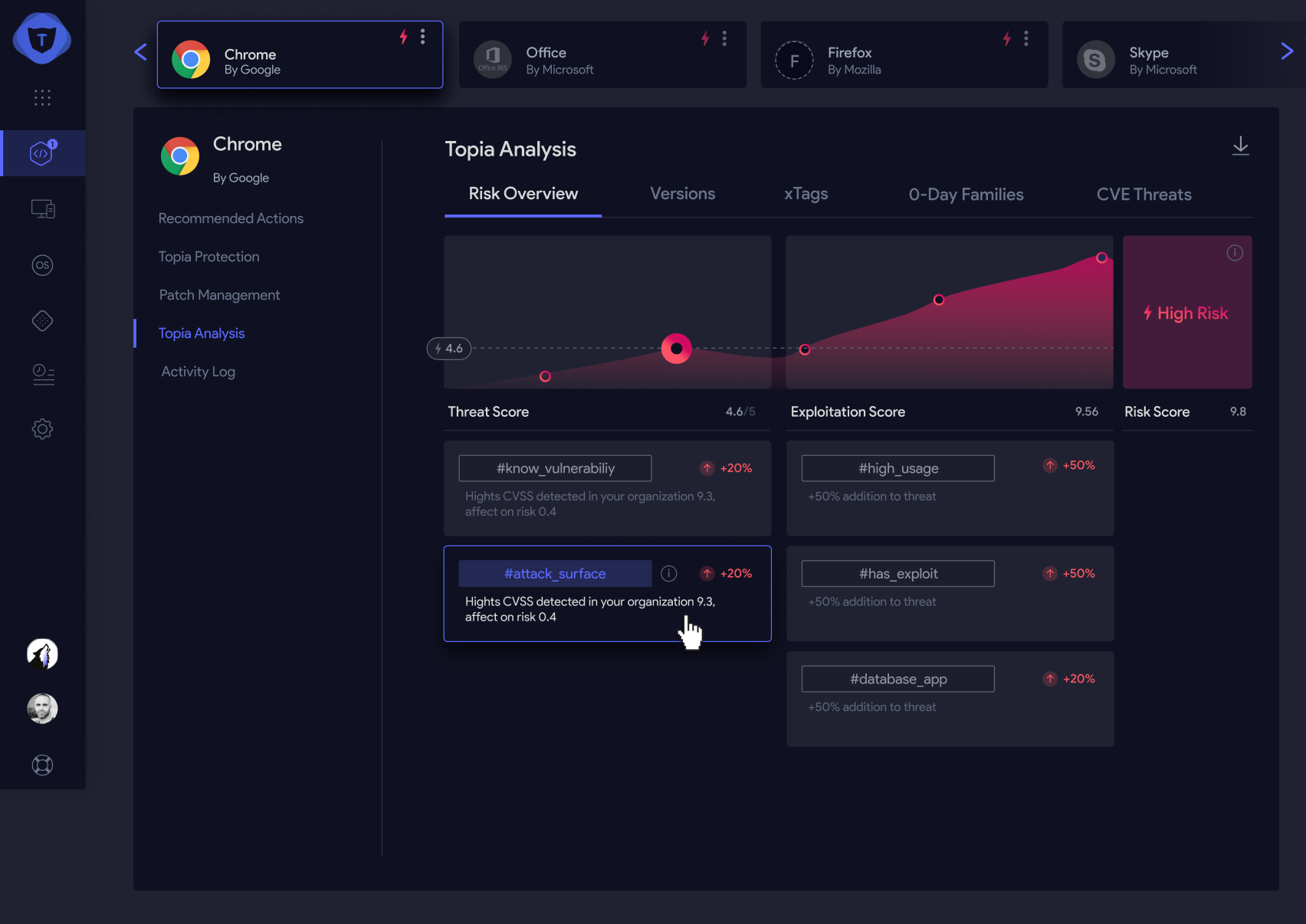
TOPIA - risk analysis screen
LIVE! On Security Weekly
Check out the video below for a Zoomtable (get it?...roundtable....Zoomtable 😜) discussion on sharpening prioritization with asset context!



