A personal experience
My first encounter with a 'Ransomware' threat had nothing to do with my workplace, but closer to my home.
Among my friends and family, I’m considered the ‘tech guy’ (I guess some of you can relate). I wasn’t that surprised getting a late night text message from a friend of mine: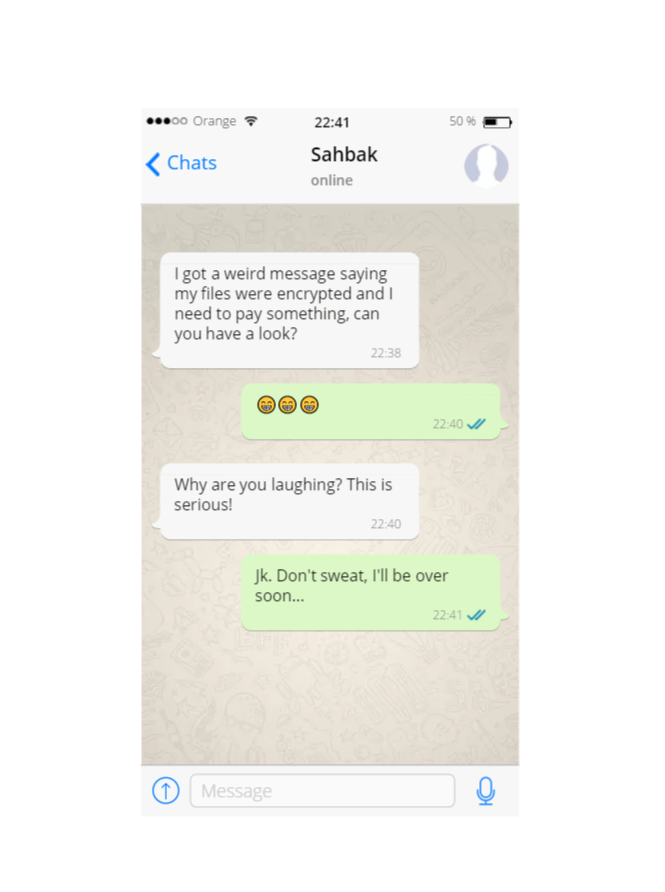
'Luckily' for him, he tends to get infected twice a month (a fascinating topic by itself) so aside from trying to educate him, I’ve prepared a remote backup just in case.
Getting hit by a ransomware is always terrifying, just the thought of your sensitive digital assets (pictures, documents, etc.) being locked away is dreadful.
As a security vendor, you always try to find novel ways to encounter existing and emerging threats. Ransomware is a challenge because late response can lead to a catastrophic outcome.
This post will discuss some of the insights we gathered through an internal research on that topic.
Analyzed threats
We will examine the common characteristics of the following samples:
- WannaCry
- Flare
- Locky
- Princess
- TeslaCrypt
- Cerber
- CryptoMix
- CryptoWall
- Petaya
- CryptoLocker
General workflow
When looking into the flow of the attack, we can identify several key steps:
- Once infected, the ransomware gathers unique information and send to C2 server
- C2 server generates an encryption key pair, and submit the public key to the infected computer
- The infected computer encrypts the files using built-in encryption capabilities
- Post-encryption, the ransomware deletes the local backups (usually shadow copies)
The infected entity is being notified and asked to pay
Techniques overview
While every attack consists of many steps, there are some that their frequency is significantly higher:
Data encryption
The bread and butter of every ransomware attack is to encrypt your data. We can notice a repetitive pattern, as the vast majority of these attacks use the built-in encryption capability of Windows.
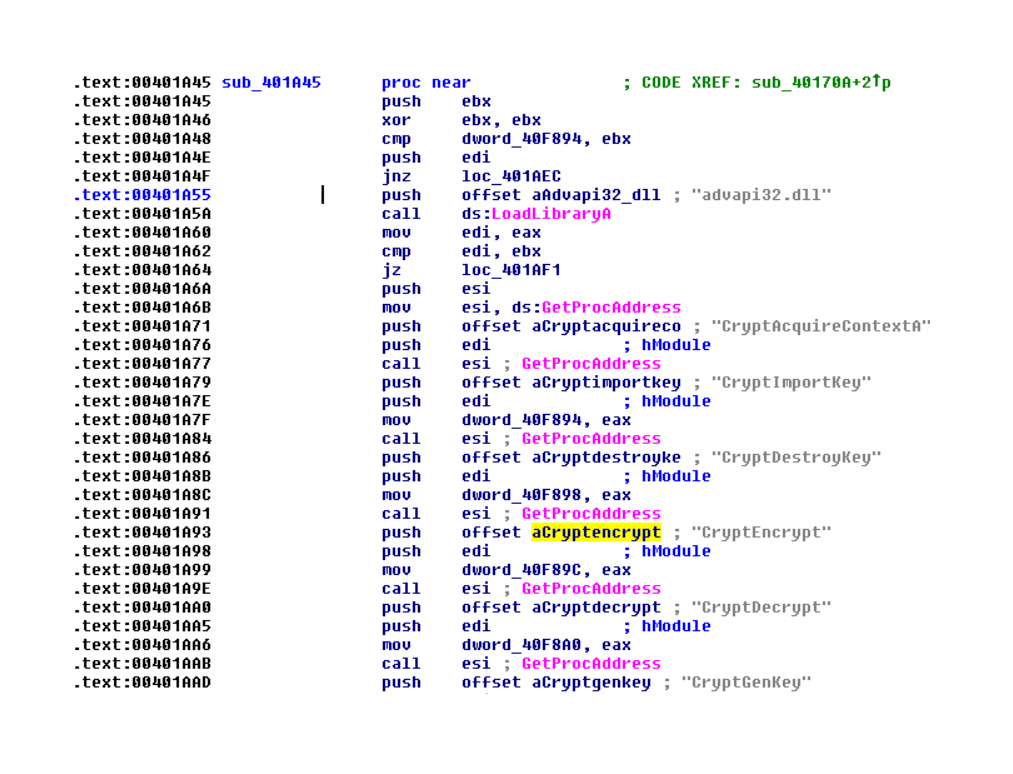
The most commonly abused function is the `CryptEncrypt` function, exported by Advapi32.dll.
WannaCry dynamic import:
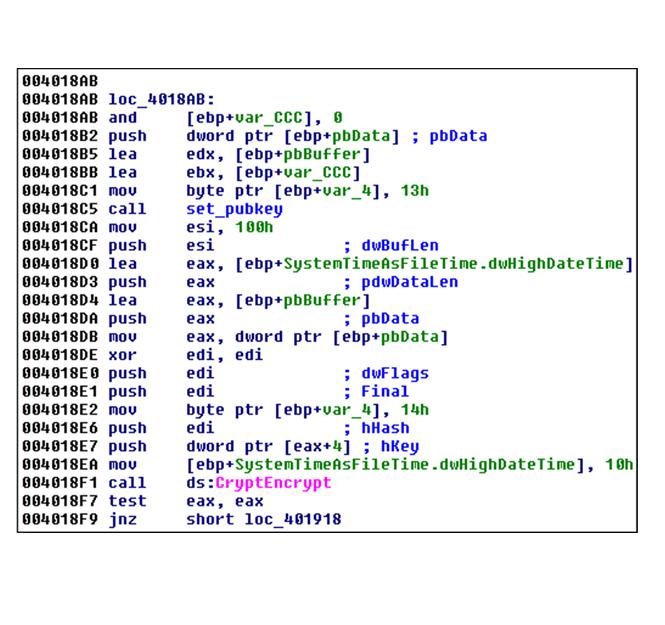
 Locky runtime call:
Locky runtime call:
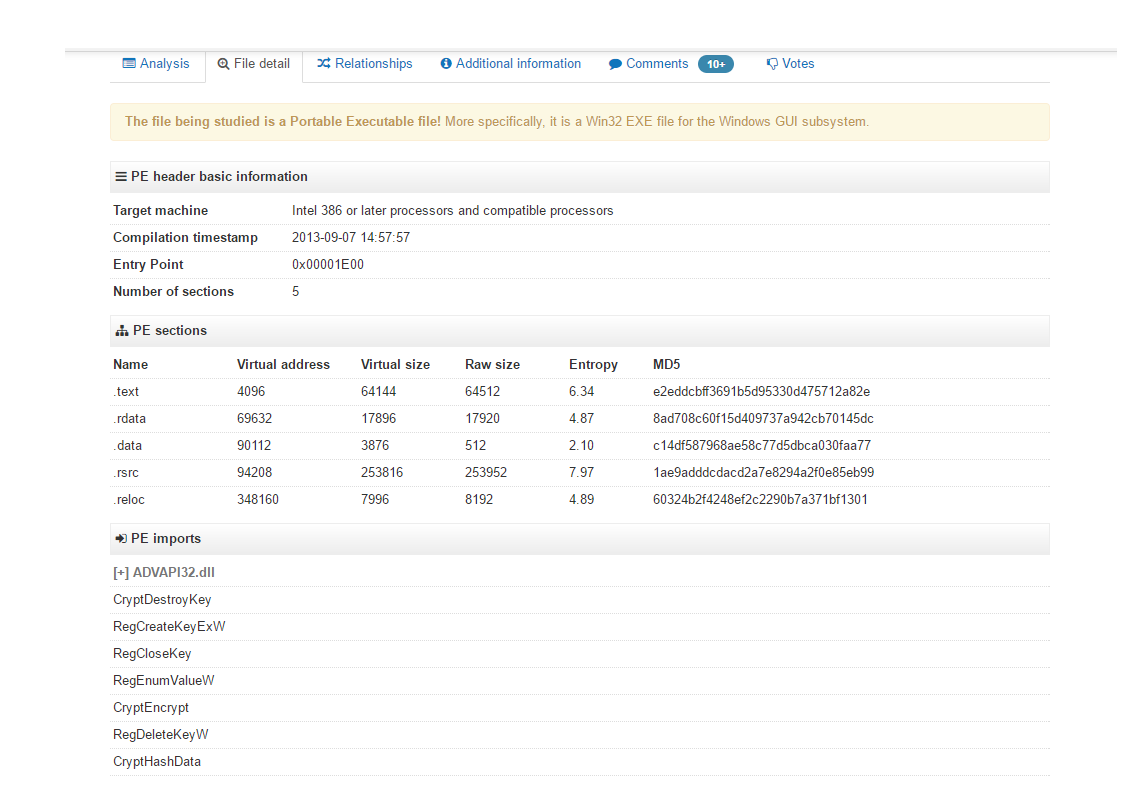
CryptoLocker static import:
VSS backup deletion (*):
The easiest way to delete the VSS backups is simply executing the following command:
* `vssadmin delete shadows /all /quiet`
Or via WMIC:
* `wmic shadowcopy delete`
Executing these two commands will send a message to the 'Volume shadow copy' service, executing the `DeleteSnapshots` method.
Service creation (*):
Not essential, but it's one of the options to ensure reboot persistence.
Some of the possible techniques:
* `sc create binpath= “ ” start= auto`
* Or just calling the `CreateService` function directly from Advapi32.dll
(*) - Requires administrative privileges
Techniques analysis
In the samples listed here, we witnessed a repetitive pattern. The vast majority of the attackers abused the existing functionalities within the OS.
When thinking about an offensive action as a profit and loss project, we can understand a few of the considerations behind the design of an offensive tool.
Let's take a deeper look into the encryption capability. There are code examples that implement a similar functionality, but developing a proprietary mechanism is hard and expensive. Also, improper/poor implementation is likely to be broken and may incur profit loss. We can assume that these were the considerations behind the ransomware developers, as we witnessed how they chose to rely on the built-in encryption capabilities of the OS.
Conclusion
When trying to tackle any threat, such as the ones listed here, we're trying to detect the 'critical path' of the attack before it is actually being abused.
Any software, Windows OS in this example, has certain functionalities that in the wrong hands will have dire results. Having a complete visibility of the risks, and the ability to take proactive measures to eliminate them becomes crucial.
In this post, you've learned that different attackers tend to choose the same 'critical path' of exploitation, abusing the same software capabilities. This pattern is not going to change.
At Vicarius, we developed a unified vulnerability management platform that can discover, evaluate and protect any software capability.



